Table of Contents
A hash function takes an input string (numbers, alphabets, media files) of any length and transforms it into a fixed length. The fixed bit length can vary (like 32-bit or 64-bit or 128-bit or 256-bit) depending on the hash function which is being used. The fixed-length output is called a hash. This hash is also the cryptographic byproduct of a hash algorithm. We can understand it from the following diagram.
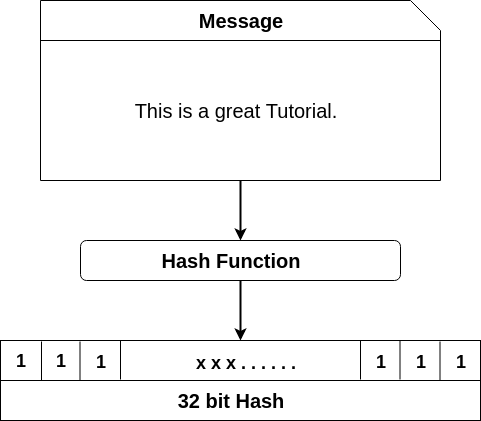
The hash algorithm has certain unique properties:
- It produces a unique output (or hash).
- It is a one-way function.
In the context of cryptocurrencies like Bitcoin, the blockchain uses this cryptographic hash function’s properties in its consensus mechanism. A cryptographic hash is a digest or digital fingerprints of a certain amount of data. In cryptographic hash functions, the transactions are taken as an input and run through a hashing algorithm which gives an output of a fixed size.
1. SHA-256
A Bitcoin’s blockchain uses SHA-256 (Secure Hash Algorithm) hashing algorithm. In 2001, SHA-256 Hashing algorithm was developed by the National Security Agency (NSA) in the USA.
2. How does the hashing process works?
For this hash function, we are going to use a program developed by Anders Brownworth. This program can be found in the below link.
Anders Brownworth Hash Program: https://anders.com/blockchain/hash.html
If we type any character in the data section, we will observe its corresponding cryptographic hash in the hash section.
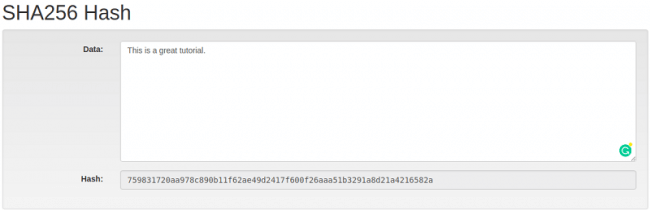
For example: We have type in data section: This is a great tutorial.
It will generate the corresponding Hash:
759831720aa978c890b11f62ae49d2417f600f26aaa51b3291a8d21a4216582a
[/code]
Now if we change the text: “This is a great tutorial.” To “this is a great tutorial.”
You will find the corresponding Hash:
4bc35380792eb7884df411ade1fa5fc3e82ab2da76f76dc83e1baecf48d60018
[/code]
In the above, you can see that we have changed only the first character case sentence from capital “T” to small “t” and it will change the whole Hash value.
Note: If we write the same text again in a data section, it will always give the same output. It is because you are creating a message digest of that one’s specific amount of data.
Since the Hash function is a one-way function, there is no way to get back entire text from the generated hash. This is different from traditional cryptographic functions like encryption where you can encrypt something using the key and by using decryption, you can decrypt the message to its original form.

